P4wnP1 Wiki¶
DISCLAIMER
This wiki is a HUGE work in progress just like the P4wnP1 project itself. The info here comes from FAQ.md, README.md, and many issues in the original project. Keep in mind this block of text won't be here forever (hopefully).
About P4wnP1¶
Introduction¶
P4wnP1 is a highly customizable USB attack platform, based on a low cost Raspberry Pi Zero or Raspberry Pi Zero W. Since the initial release in February 2017, P4wnP1 has come along way. A lot of the time has been spent troubleshooting new features and bugs in the old.
P4wnP1 Features¶
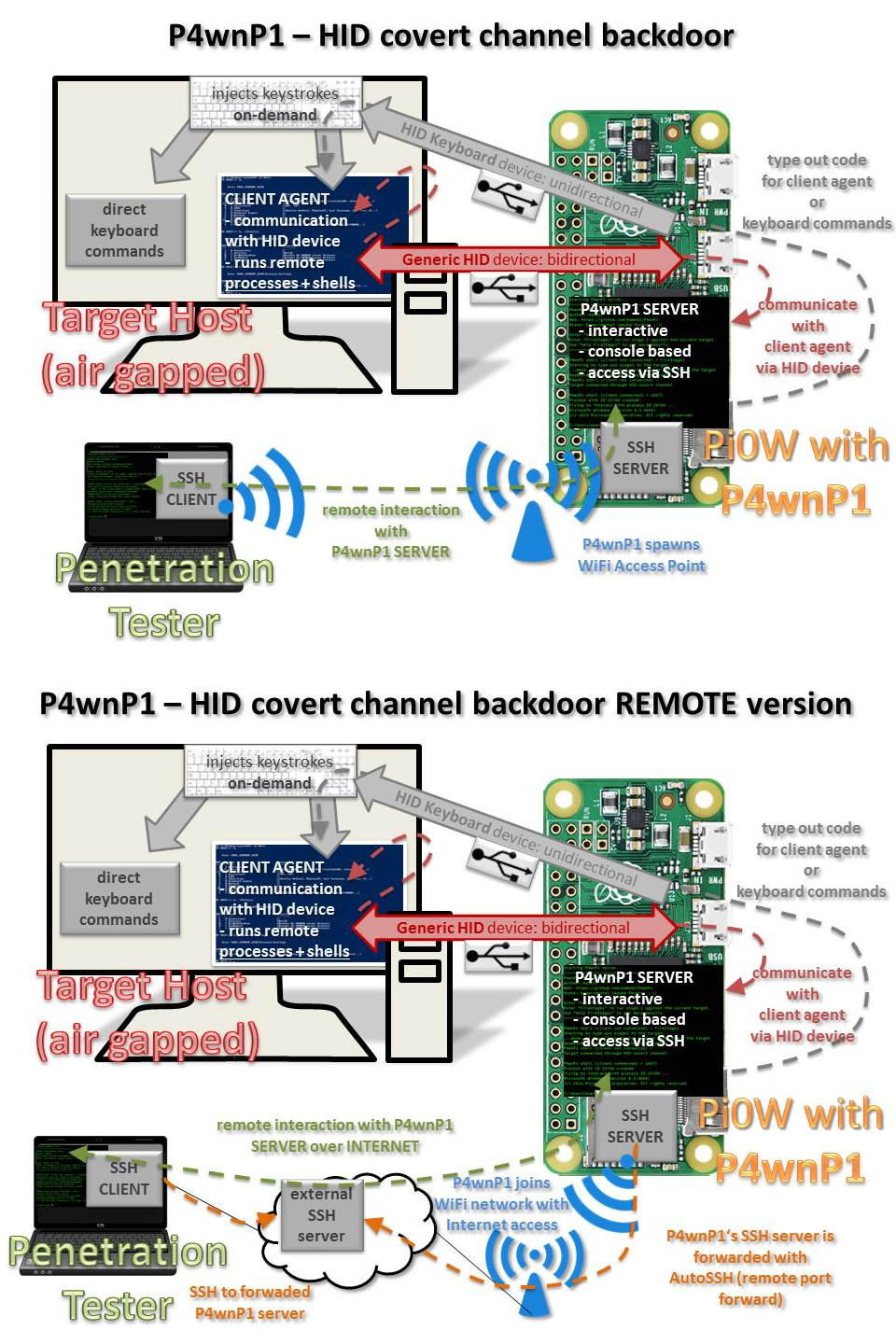
- HID covert channel Frontdoor/Backdoor | Get remote shell access to Windows targets via HID devices)
- Windows 10 Lockpicker | Unlock Windows boxes with weak passwords (fully automated)
- Stealing Browser Credentials | Dumps stored Browser Credentials and copys them to the builtin flashdrive
- WiFi Hotspot | SSH access (Pi Zero W only), supports hidden ESSID
- Client Mode | Relays USB net attacks over WiFi with internet access (MitM)
- USB device | Works with Windows Plug and Play support
- Device Types:
- HID covert channel communication device | Frontdoor/Backdoor
- HID Keyboard/Mouse
- USB Mass storage | Currently only in demo setup with 128 Megabyte drive
- RNDIS | Windows Networking
- CDC ECM | MacOS / Linux Networking
- Bash based payload scripts | See
payloads/subfolder for examples example - Responder
- John the Ripper Jumbo | Pre-compiled version ready to go
- AutoSSH integration | For easy reverse ssh tunnels
- Auto attack | P4wnP1 automatically boots to standard shell if an OTG adapter is attached
- LED state feedback | with a simple bash command (
led_blink) - Advanced Features
Communication¶
Feature Comparison with BashBunny¶
Some days after initial P4wnP1 commit, Hak5's BashBunny was announced (and ordered by myself). Here's a little feature comparison:
| Feature | BashBunny | P4wnP1 |
|---|---|---|
| RNDIS, CDC ECM, HID , serial and Mass storage support | supported, usable in several combinations, Windows Class driver support (Plug and Play) in most modes | supported, usable in most combinations, Windows Class driver support (Plug and Play) in all modes as composite device |
| Target to device communication on covert HID channel | no | Raw HID device allows communication with Windows Targets (PowerShell 2.0+ present) via raw HID There's a full automated payload, allowing to access P4wnP1 bash via a custom PowerShell console from target device (see 'hid_frontdoor.txt' payload). An additional payload based on this technique, allows to expose a backdoor session to P4wnP1 via HID covert channel and relaying it via WiFi/Bluetooth to any SSH capable device (bridging airgaps, payload 'hid_backdoor.txt') |
| Mouse emulation | no | Supported: relative Mouse positioning (most OS, including Android) + ABSOLUTE mouse positioning (Windows); dedicated scripting language "MouseScript" to control the Mouse, MouseScripts on-demand from HID backdoor shell |
| Trigger payloads via target keyboard | No | Hardware based: LEDs for CAPSLOCK/SCROLLLOCK and NUMLOCK are read back and used to branch or trigger payloads (see hid_keyboard2.txt payload) |
| Interactive DuckyScript execution | Not supported | supported, HID backdoor could be used to fire scripts on-demand (via WiFi, Bluetooth or from Internet using the HID remote backdoor) |
| USB configuration changable during runtime | supported | will maybe be implemented |
| Support for RubberDucky payloads | supported | supported |
| Support for piping command output to HID keyboard out | no | supported |
| Switchable payloads | Hardware switch | manually in interactive mode (Hardware switch could be soldered, script support is a low priority ToDo. At least till somebody prints a housing for the Pi which has such a switch and PIN connectors) |
| Interactive Login with display out | SSH / serial | SSH / serial / stand-alone (USB OTG + HDMI) |
| Performance | High performance ARM quad core CPU, SSD Flash | Low performance single core ARM CPU, SDCARD |
| Network interface bitrate | Windows RNDIS: 2 GBit/sLinux/MacOS ECM: 100 MBit/sReal bitrate 450 MBit max (USB 2.0) | Windows RNDIS: 20 GBit/sLinux/MacOS ECM: 4 GBit/s (detected as 1 GBit/s interface on MacOS)Real bitrate 450 MBit max (USB 2.0)Here's the needed P4wnP1 patch |
| LED indicator | RGB Led, driven by single payload command | mono color LED, driven by a single payload command |
| Customization | Debian based OS with package manager | Debian based OS with package manager |
| External network access via WLAN (relay attacks, MitM attacks, airgap bridging) | Not possible, no external interface | supported with Pi Zero W |
| SSH access via Bluetooth | not possible | supported (Pi Zero W) |
| Connect to existing WiFi networks (headless) | not possible | supported (Pi Zero W) |
| Shell access via Internet | not possible | supported (WiFi client connection + SSH remote port forwarding to SSH server owned by the pentester via AutoSSH) |
| Ease of use | Easy, change payloads based on USB drive, simple bash based scripting language | Medium, bash based event driven payloads, inline commands for HID (DuckyScript and ASCII keyboard printing, as well as LED control) |
| Available payloads | Fast growing github repo (big community) | Slowly growing github repo (spare time one man show ;-)) Edit: Growing community, but no payload contributions so far |
| In one sentence ... | "World's most advanced USB attack platform." | A open source project for the pentesting and red teaming community. |
| Total Costs of Ownership | about 99 USD | about 5 USD (11 USD fow WLAN capability with Pi Zero W) |
SumUp: BashBunny is directed to easy usage, but costs 20 times as much as the basic P4wnP1 hardware. P4wnP1 is directed to a more advanced user, but allows outbound communication on a separate network interface (routing and MitM traffic to upstream internet, hardware backdoor etc.)
External Resources using P4wnP1¶
- Dan The IOT Man, Introduction + Install instructions "P4wnP1 – The Pi Zero based USB attack-Platform": Dan the IOT Man
- Black Hat Sessions XV, workshop material "Weaponizing the Raspberry Pi Zero" (Workshop material + slides): BHSXV
- ihacklabs[dot]com, tutorial "Red Team Arsenal – Hardware :: P4wnp1 Walkthrough" (Spanish): part 1, part 2, part 3
Credits to¶
- Seytonic, youtube channel on hacking and hardware projects
- Rogan Dawes, Sensepost, core developer of Universal Serial Abuse - USaBUSe
- Samy Kamkar, PoisonTap
- Rob ‘MUBIX’ Fuller, “Snagging creds from locked machines”
- Laurent Gaffie (lgandx), Responder
- Darren Kitchen (hak5darren), DuckEncoder, time to implement a WiFi capable successor for BashBunny ;-)
- All of the Github supporters